I - vengers: Identity Wars
\
\ What an efficient label to encapsulate such a concept of great practical and philosophical depth. Like an ominous name pronounced by a wise sage with outstretched arms to capture a rather illusive and mysterious phenomenon. Picture yoda making that discovery.
\
\ A rather more general term though, this article will be focusing on a more specific aspect of Identity known as digital identity. Digital identity is basically how your information is managed online for proper identification and management. Digital identity is something that we rarely think about in our day-to-day lives, but it is something that we all have subscribed to.
\ Currently, the average person, and likely you reading this, has over 150 accounts online, each with a separate username, password and security process. Think of the likes of Facebook, X (Twitter), Instagram, Signal, Amazon, Telegram, Deliveroo, Uber… the list goes on.
\ Every time we open an account online, to use a service, buy something online, use social media, or even just browse the internet, we are creating a digital footprint for ourselves, which feeds into a digital profile. And each of these different accounts holds personal data about you, such as your name, age, photographs, sex, gender etc., and also various preference data, such as what you browse, like, share or click on. These digital profiles are generally secured behind a password, meaning that you feel a level of confidence that you have control over them.
\
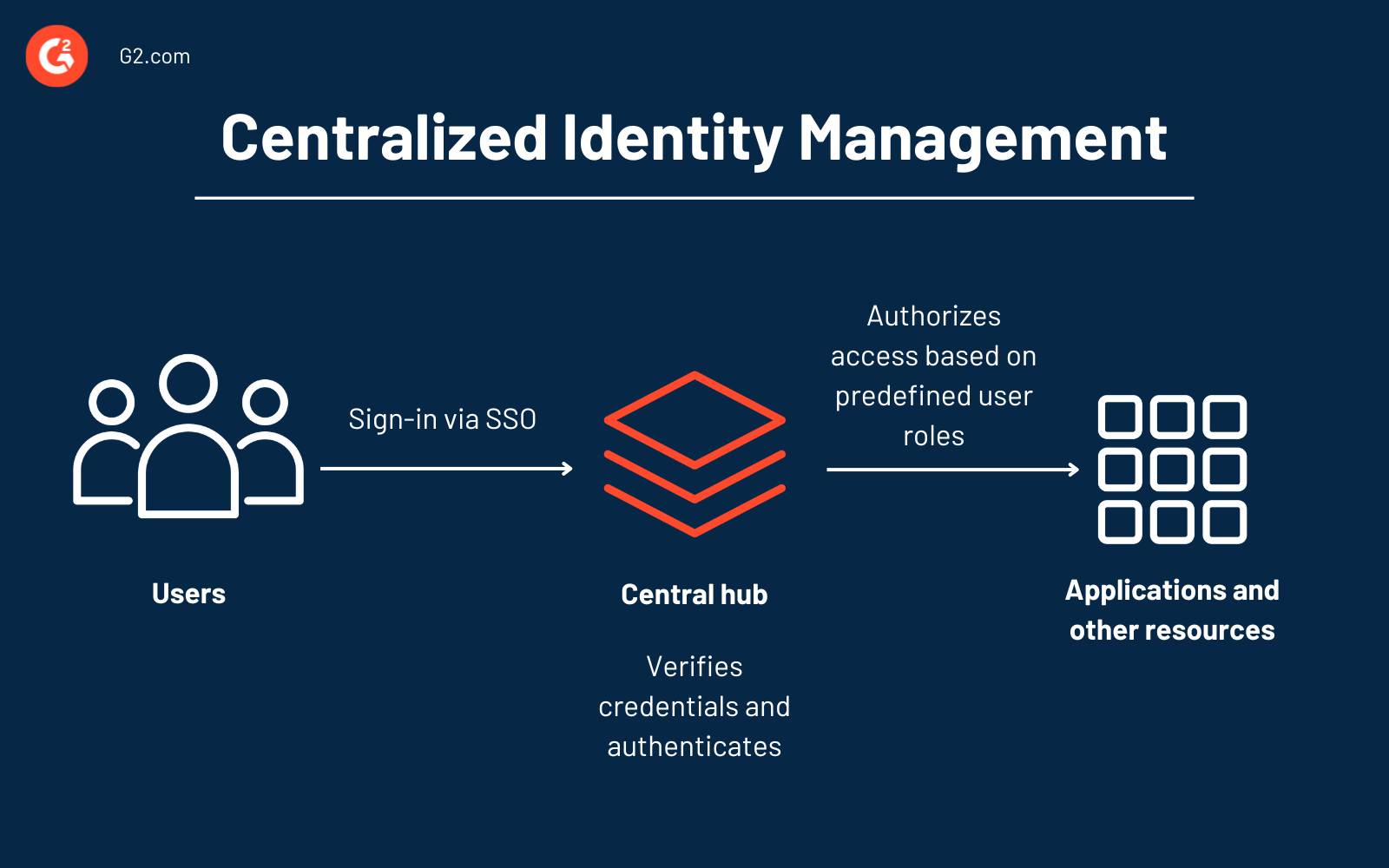
However, in reality this is not the case. Our data is stored across multiple gated siloes, and every time we want to access this data, we need to prove to the gatekeeper that we are who we claim to be through an authentication process. In other words, every time you want to get access to your own digital identity data, you need to get through a locked door using a key. This established way of managing digital identity is known as centralized identity management.
\ There are many problems with this model and a few of them are as follows:
\
-
Data is vulnerable to breaches from a single point of failure (i.e. the server)
-
Companies can do as they please with user data e.g. selling to ad companies.
-
Difficulty in managing user data across several accounts.
\
These numerous problems have predictably resulted in the rise of several innovations to offer alternative identity management solutions in cyberspace creating a rather entertaining identity management war.
\ Identity Wars?
\
\ Well, you may find the topic “I - vengers: Indentity Wars” rather nerdy right?
\ Lol… me too.
\ However, the tech field can be quite difficult to understand and as the alpha nerd of this story I'd rather carry everyone along with what I believe to be a more friendly reference - The Avengers series.
\ Let's summarize our introduction like this.
\
\
\ We shall now proceed to explore these models and technologies in detail.
\
Types of identity management.
\
-
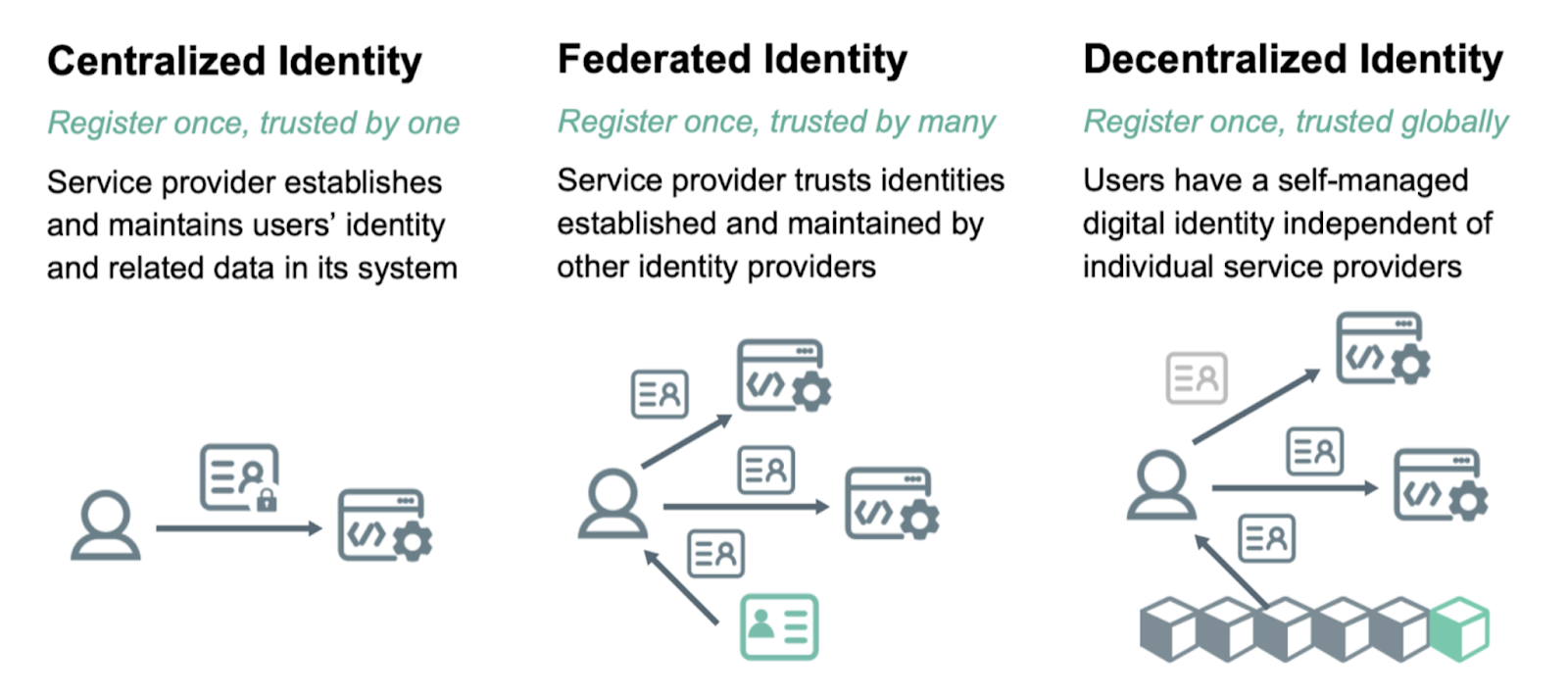
Centralized Identity Model:
\ Here, all user identity data like usernames, passwords etc. is stored in a single, central location. It is easy to manage and scale, however, there is a single point of failure. If the central database is compromised, all user data could be exposed.
\
Examples Of Centralized Identity Models
\ I. Directory Service is a centralized identity system that stores user information in a central database for authentication and access. For example, Yahoo small business.
Yahoo small business provides web hosting, domain registration, and business related services for small businesses. The directory website design is user friendly and well structured, with clear navigation menus. It provides essential information for small business owners.
\ II. Identity Federation is a system that allows users to authenticate to multiple websites and applications using a single set of credentials. For example, academic websites like claerine.eu.
A university student can use their identity federation credentials to sign in to the university's website, the library's website, and the student union's website. The student only has to remember one set of credentials and their identity is verified once by the central identity provider.
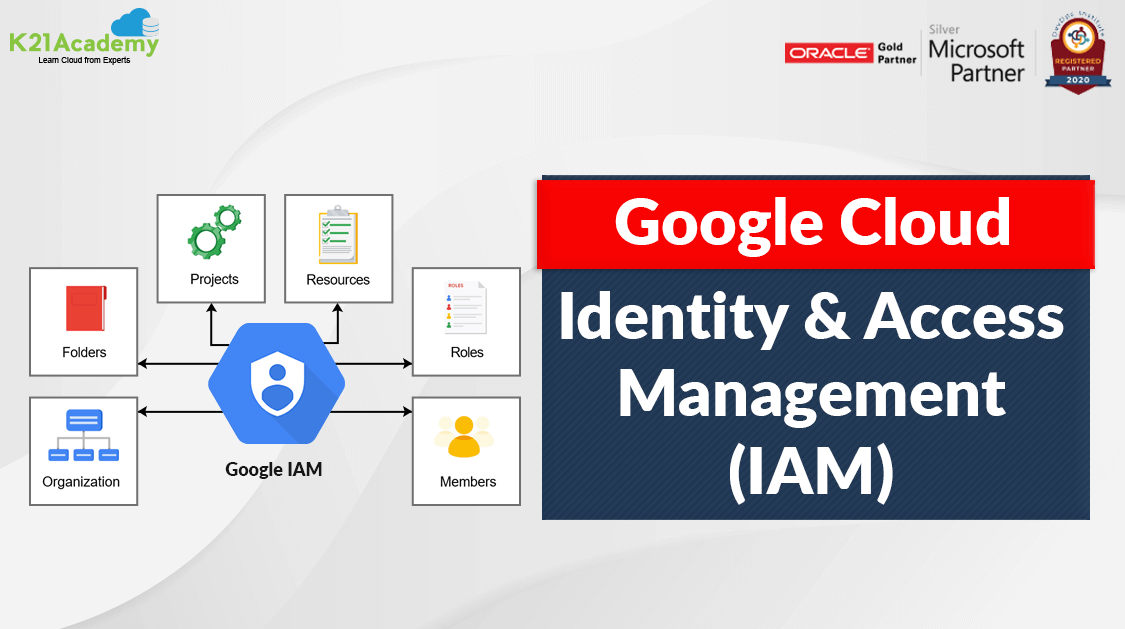
\ III. Cloud-based Identity Management Platforms is a system that can be used to manage user access to applications and resources. Such platforms offer a variety of features, including single sign-on, multi-factor authentication, and user provisioning. For example, Google Cloud.
A company can use a cloud-based identity management platform to manage user access to its internal applications, such as its email system and its customer relationship management (CRM) system. It can also be used to manage user access to external applications.
\
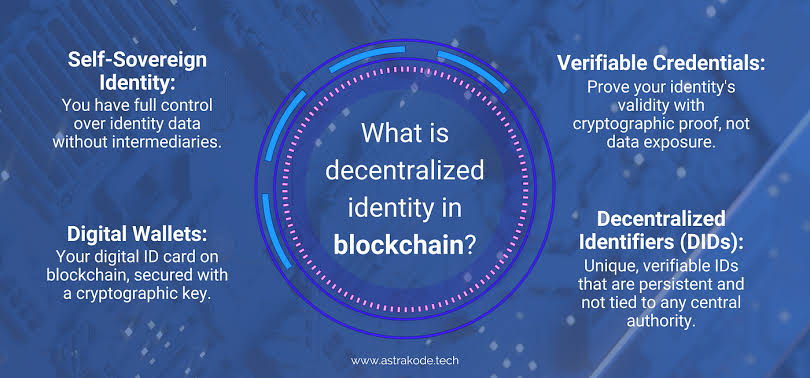
2. Decentralized Identity Model:
In this model, user identity data is distributed across multiple locations. This data is stored securely, and it is only accessible to the user and the entities that the user has authorized to access it.
Decentralized identity models offer several advantages over centralized identity models. They are more secure, as there is no single point of failure. They are also more user-friendly, as users only have to manage one set of credentials.
However, decentralized identity models can be more difficult to manage and scale than centralized identity models. Also, they may not be compatible with all existing applications and systems.
\
Examples Of Decentralized Identity Models
\
-
Blockchain is a distributed ledger technology that can be used to create decentralized identity systems. In a decentralized identity system using blockchain, users' identity data is stored in a tamper-proof distributed ledger. This data is only accessible to the user and the entities that the user has authorized to access it. For example, cheqd.io.
cheqd is a blockchain network, built in the Cosmos ecosystem, designed to achieve three core missions:
-
To enable individuals and organisations to have digital, trustworthy interactions directly with each other, whilst maintaining privacy and without any centralised intermediary needed.
-
To facilitate the creation of new trusted ecosystems or business models across several industries, through the decentralised identity and Verifiable Credentials technology, plus the use of their token $CHEQ for credential payments.
-
To bridge the DeFi ecosystem with the decentralised identity ecosystem, for better user experiences, democratic governance, regulatory compliance and operational efficiency.
\
-
Self-Sovereign Identity (SSI) is a decentralized identity model that gives users control over their identity data. In an SSI system, users own their identity data and can share it with entities that they trust. Users can also revoke access to their identity data at any time.
SSI systems are based on several key principles:
- Self-ownership of all user data.
- Portability of data between users.
- Interoperability between SSI systems.
For example cheqd SSI and Nordivo.
Nordivo enables you to engage with decentralized identity for your products and services and plug into the new identity layer of the internet with verifiable credentials.
\ Verifiable Credentials (VC), are digital credentials that can be verified by anyone, can be used to verify a person's identity, education, or other attributes. For example, students can use VC to prove their academic achievements to potential employers or universities. This can help to reduce the need for paper transcripts and make it easier for students to transfer credits between institutions.
\
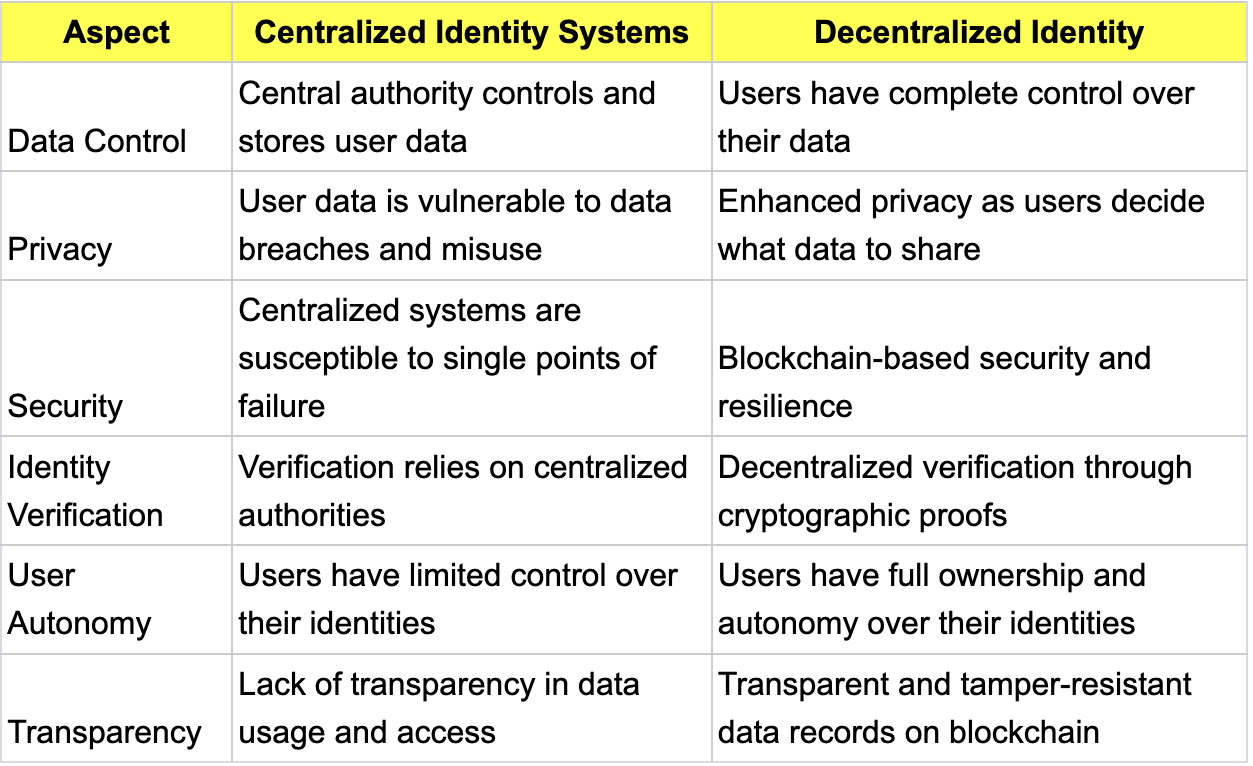
Centralized Identity Versus Decentralized Identity.
The flier below compares centralized identity management and decentralized identity management under several key aspects.
\
As you can see, each of the models has their area of strength and weakness but decentralized models tend to have more advantages than disadvantages.
\
Which model do I want?
The model you should consider depends on your specific needs. Are you building a product or you're just a user? What kind of product are you building? What's your budget and long term plan?
\
\ Whatever the answer is below are some factors you should consider before making a choice.
\
- The size and complexity of your company: If you have a small company with a few employees, you may be able to get away with using a simple centralized identity management solution. However, if you have a large company with a complex IT infrastructure, you will need a more robust and scalable solution.
- The types of applications and systems that you use: If you use a lot of different applications and systems, you will need an identity management solution that can integrate with all of them. This can be a challenge, as not all identity management solutions are compatible with all applications and systems.
- The security requirements of your company: If you have a high-security environment, you will need an identity management solution that can provide a high level of security. This may require a solution that uses two-factor authentication, single sign-on, and other security features.
- The budget that you have available: Identity management solutions can range in price from a few hundred dollars to several thousand dollars. You will need to decide how much you are willing to spend on an identity management solution, and then choose a solution that fits your budget.
- The future growth of your company: If you are planning on growing your company shortly, you will need to choose an identity management model that can scale with your growth.
- The needs of your users: You will need to choose an identity management model that is easy for your users to use. This is especially important if you have a large number of users or if your users are not tech-savvy.
\
In Conclusion:
Welcome audience to the end of this briefing. You've explored the digital identity wars in great detail. As a user or developer of this technology, you've been equipped with all the necessary information to take a winning position on your digital identity campaign. You shall now explore the technologies highlighted or share this piece to spread the identity gospel.
\
\
\
You May Also Like

Kalshi Partners with Solana & Base to Launch KalshiEco Hub for Onchain Prediction Markets

GBP trades firmly against US Dollar